E-Mail Oversight & Supervision For SEC 71a-4 Compliance
Email Oversight & Supervision
Today we will investigate the supervisory & oversight functions in Office 365. We will see how they can be applied in scenarios where email supervision is required due to regulatory compliance requirements or client needs. Some of the scenarios may include a need to meet SEC 71a-4 requirements placed on financial advisers or other professional service organizations that need to monitor email communication of their employees.
Background
Typically, organizations that work in highly regulated industries or that are at high risk of brand damage or intellectual property leakage require oversight of the organizations email communication to ensure company or legal policy compliance and protect organization assets such as their brand or intellectual property.
The process is typically conducted by a proprietary and expensive, journaling and governance products. However, with the introduction of data governance features in Office 365, this highly desirable capability in now with in reach of the smallest organization.
Lets examine three use cases where a policy driven data governance implementation in Office 365 can achieve the desired capabilities with minimal investment with the correct configuration.
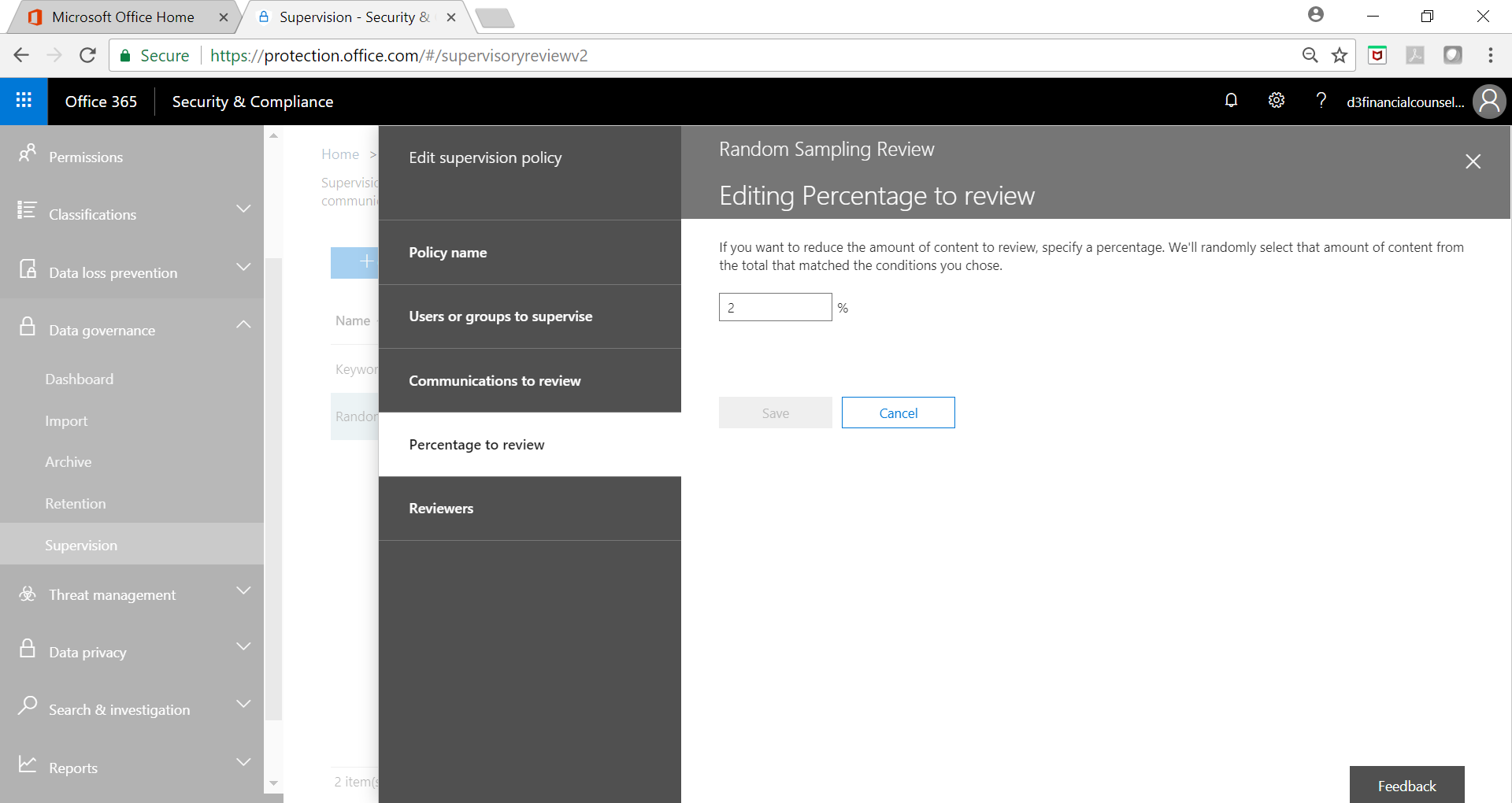
Use Case 1 – Implementing Random Sampling To Prevent Compliance Circumvention
The first of the typical use cases is a highly regulated industry client such as a financial advisory firm, a law firm or a accounting firm that wants to ensure that the communication with client follows the law or ethics guidelines.
In such a case, monitoring every email being exchanged with client is not feasible. Instead, a randomized sample taken from the email communication and directed towards the auditor or supervisor will function as ample deterrence and prevent gaming the system. A randomized sample prevents email users from figuring out key word searches and circumventing them as a completely random review simply cannot be prevented.
Below screenshot shows one such policy implementation:
Governance Policy Filter
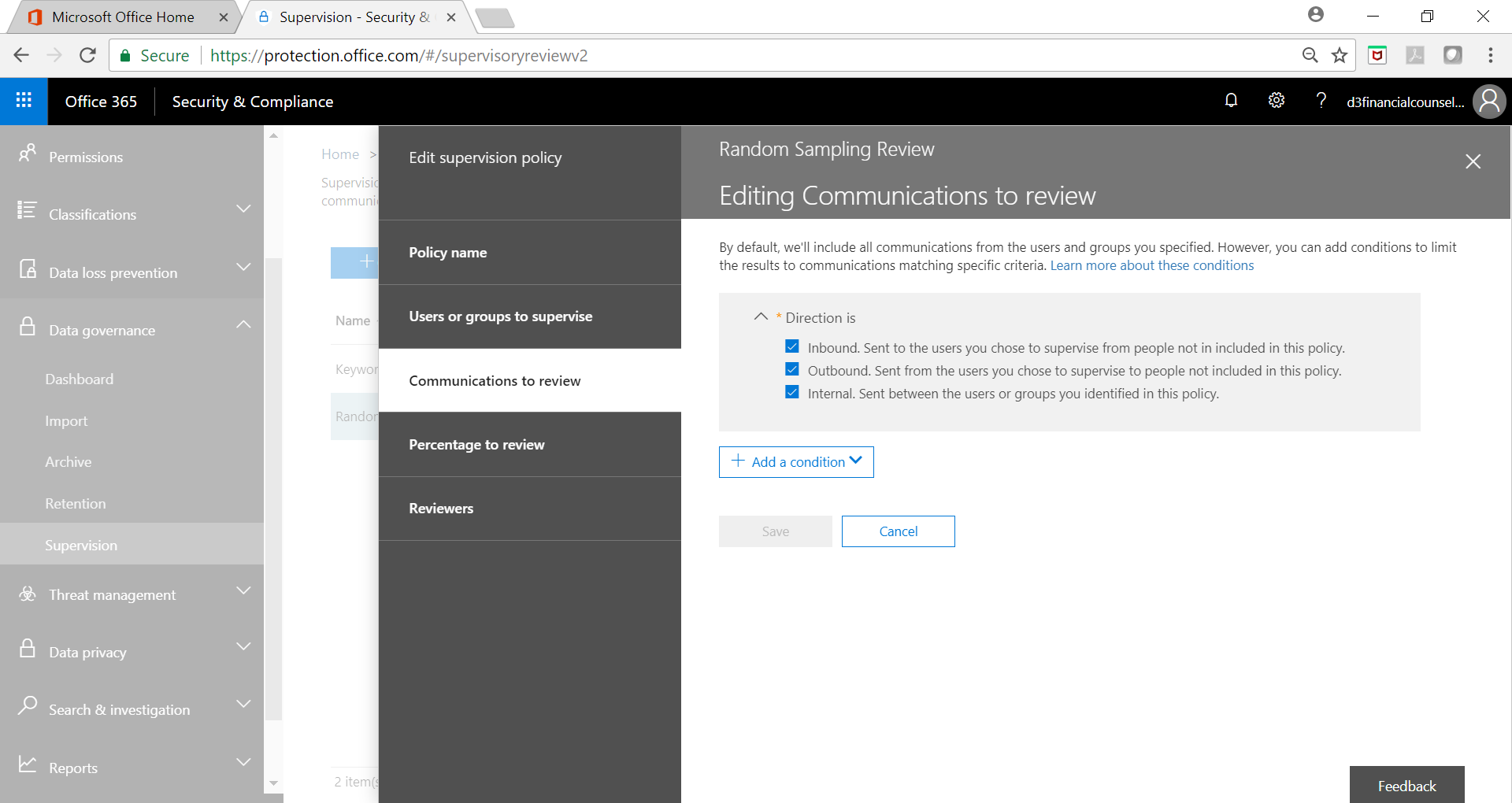
Use Case 2 – Key Word Search To Ensure Compliance
Use Case 2 – Key Word Search To Ensure Compliance
In a customer focused organization, a wayward communication with the customer by service representatives can present serious challenges to the brand. One possible solution to this problem is implementation of a keyword based search capability that looks for emotionally charged or sensitive words.
Note that this is different from implementing filters that block emails containing foul language. While content filtering is required, its also crucial to implement controls around the nature and process of communication with customers when a service representative may not present the best tone of voice.
A prudent organization would ensure that their customer representatives do not seem aloof, condescending or lackadaisical in their communication.
Below screenshots show a sample key word policy implementation:
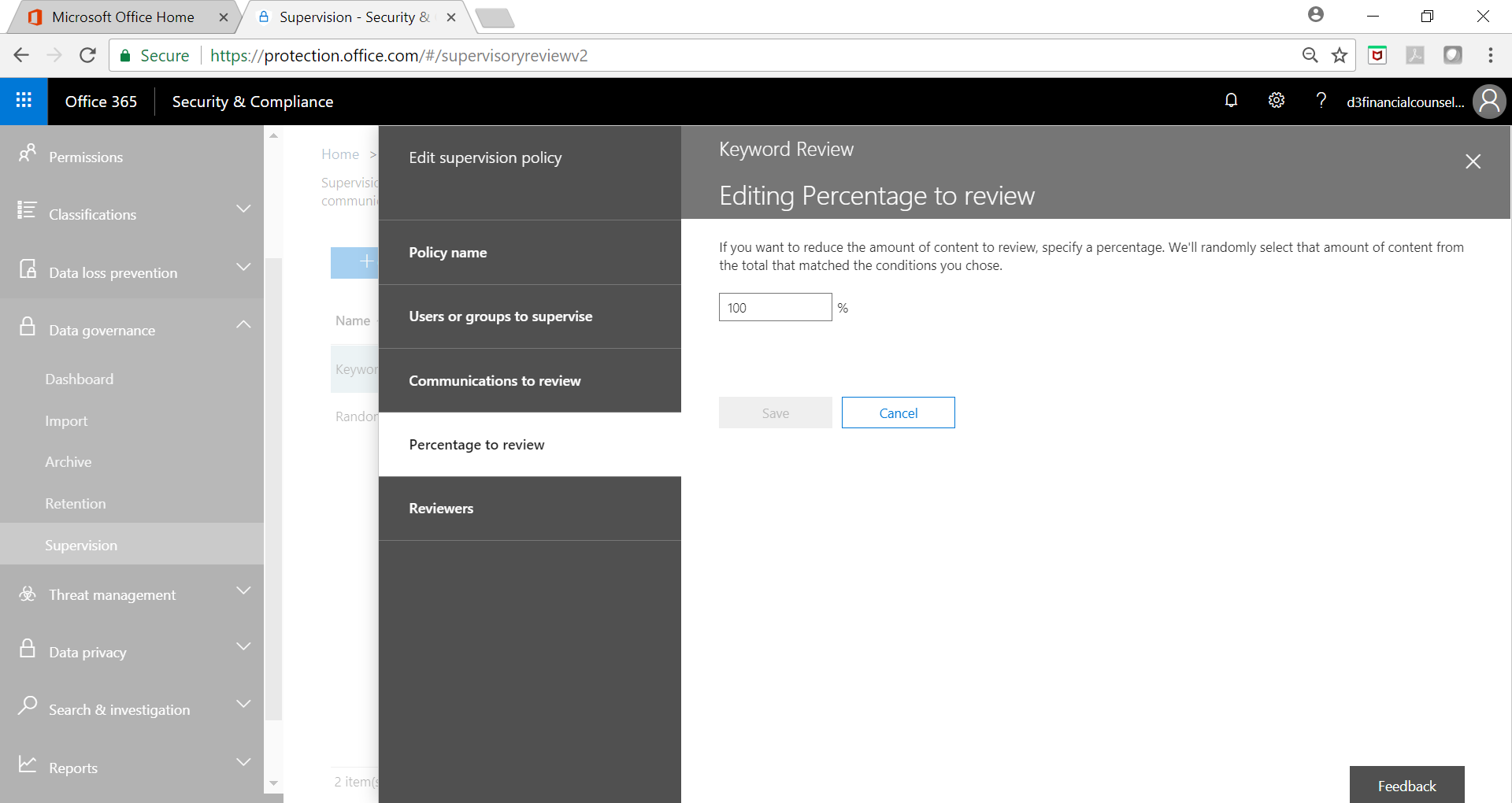
Sample Size Selection
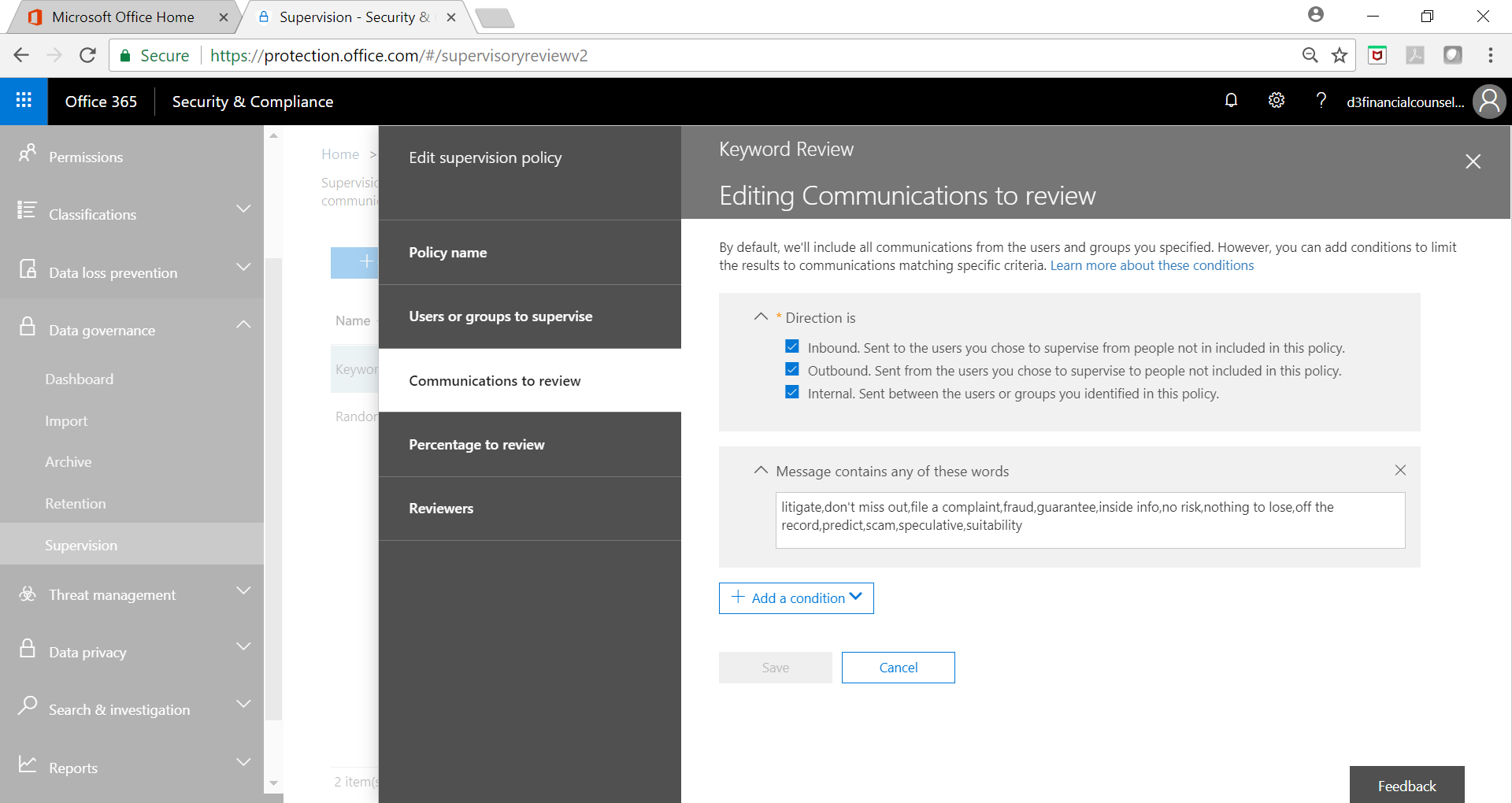
Key Word Criteria Selection
Use Case 3 – The client with a large IP to protect
Use Case 3 – The client with a large IP to protect
In the case of clients that have intellectual property that needs protection, IRM capabilities provide significant capabilities however, they do not prevent scenarios where content isn’t marked correctly or takes a different form.
In such scenarios, part of the email traffic that is outbound with a certain attachment type or size can be directed to supervisory oversight.
Conclusion
Conclusion
Implementing compliance related policies has become a relatively simple and inexpensive process that can be used by small businesses to achieve the same level of protection and oversight that has been the domain of companies with large compliance budgets. If you want to learn more about data governance features of Office 365 or how you can implement them in your organization, we provide a complimentary technical assessment that you can benefit from. Please fill the assessment request form located at Technical Assessment. If you have questions or comments about this article or any other services we provide, please Contact Us.
Klio Systems, Inc. is a technology company focused on software engineering, digital presence, managed IT services and security practices company.